Onboarding New Customers to VRS with OCI-Compliant Credentials
Use Case: Streamlining Secure Onboarding and Access Control with OCI-Compliant Credentials
Summary
Movilitas.Cloud wanted to provide a mobile app that would allow its users to access a network with stringent security requirements. This network requires Movilitas.Cloud to determine the authentication and authorization status of their customers accessing the network. Initial onboarding and ongoing user status monitoring take time and effort.
OCI-compliant digital credentials can already be used within the network for authentication and authorization purposes. Movilitas.Cloud saw an opportunity to leverage their customers’ credentials during user onboarding and status monitoring to save time and effort. Consequently, these processes have been outsourced to a trusted specialized service provider, i.e., the OCI-compliant credential issuer.
Introduction
Downloadable apps pose serious challenges for organizations that need to control who can access their services or data. Whether it’s for compliance, security, or business integrity, app providers must ensure that only verified, authorized users are allowed in.
Key challenges include:
Preventing anonymous or fraudulent access
Reducing the cost and time of manual onboarding
Ensuring auditability and traceability
Maintaining secure, role-based access over time
Traditional onboarding methods—manual reviews, custom integrations, or proprietary systems—are often slow, expensive, and hard to scale.
Context: Existing Industry Practices
Within the US pharmaceutical industry, the Verification Router Service (VRS) providers have long addressed these challenges by using Open Credentialing Initiative (OCI)-compliant Verifiable Credentials. These credentials are used to authenticate and authorize trading partners involved in product verification requests and responses. This ensures that only U.S. Drug Supply Chain Security Act (DSCSA)-compliant entities can exchange sensitive verification data, maintaining the integrity and trustworthiness of the network.
OCI-compliant credentials are cryptographically secure, interoperable, and verifiable, making them ideal for regulated environments.
Onboarding Before:
Onboarding After:
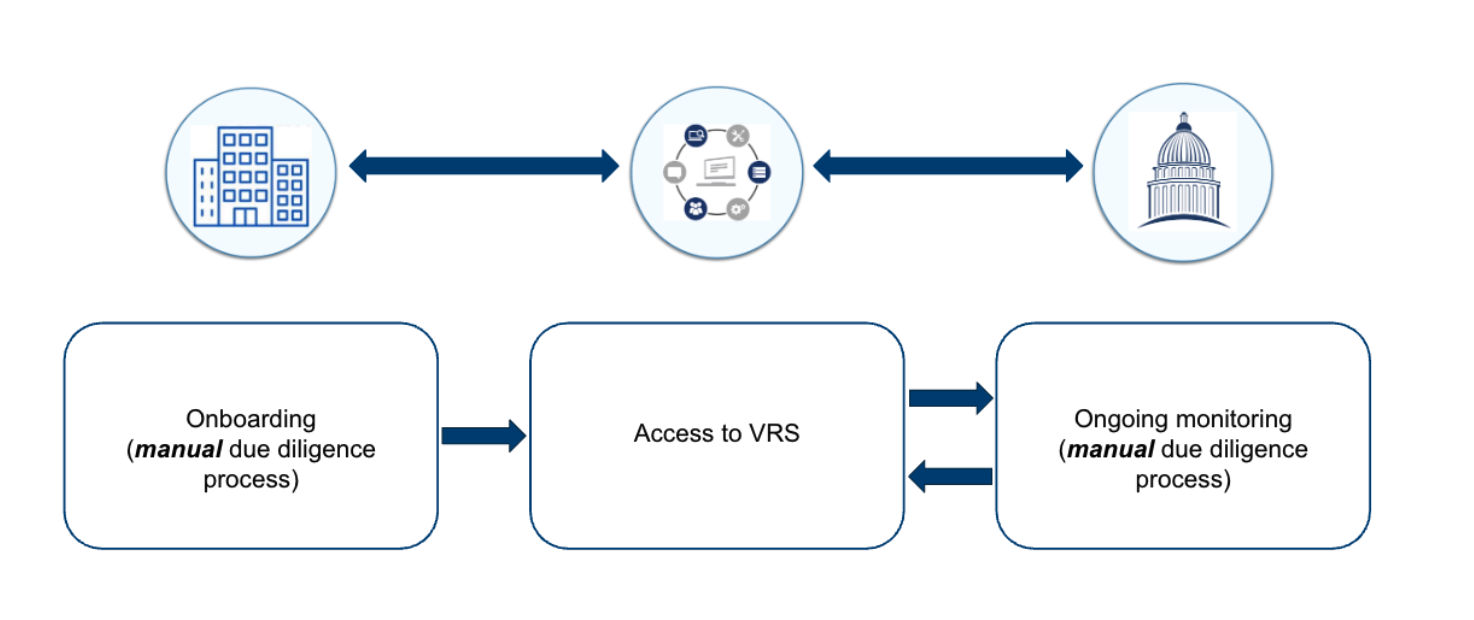
Movilitas.Cloud’s Approach
Movilitas.Cloud has extended the use of OCI-compliant credentials beyond traditional identity verification by embedding them directly into the onboarding and access control process of its mobile application, Movilitas DSCSA.
Instead of building a custom onboarding flow, Movilitas.Cloud enables new users to register using a credential issued by a supported wallet provider. This credential verifies the user’s identity and business status.
How It Works
Download: The user installs the Movilitas DSCSA app from the App Store or Google Play.
Request Credential: Within the app, the user requests a credential from a supported wallet provider.
Access Granted: Once verified, the credential is used to authenticate the user and authorize their digital interactions.
This process can be completed in minutes and only needs to be done once—unless the credential status changes.
Ongoing Credential Monitoring
What sets this approach apart is that the credential isn’t just used once. The status of the credential is continuously monitored. If the user’s authorization changes, e.g. due to revocation or expiration, the system automatically revokes access.
This ensures that access control remains accurate and up to date without requiring manual intervention, extending the efficiency gains well beyond initial onboarding.
Benefits
Faster, frictionless onboarding
Verified, non-anonymous access
Reduced operational overhead
Stronger security and compliance
Credential reuse across systems
Dynamic access control through ongoing monitoring
Conclusion
Movilitas.Cloud’s use of OCI-compliant credentials shows how app providers can modernize onboarding and access control. By combining secure digital identity with real-time credential validation and monitoring, organizations can build trust, reduce risk, and scale more efficiently—regardless of industry.